The threat of cyberattacks grows each year. According to a recent survey by Pew, cyberattacks now rank as one of the top global threats alongside climate change and terrorism. Attacks are becoming more complex and sophisticated. Malicious actors are now in control of vast resources including massive username and password data dumps that can be used to launch ransomware, distributed denial-of-service (DDoS), and data breach attacks against target networks.
For businesses, cybersecurity should now be an intrinsic part of operations. Falling victim to cyberattacks can have dire consequences. Downtime, loss of intellectual property, and reputation damage can all have significant financial costs. Even governments aren’t sympathetic to companies that get breached due to lax security. Data protection regulations can levy significant fines on companies that fail to protect customer data.
We recently met with Diane Rogers, Product Manager of Realtime Security of IT management platform Cloud Management Suite, to discuss what cybersecurity has in store for companies this year.
Cyberattacks have been a hot topic over the past years. What’s in store for us in 2019?
It’s generally believed that getting attacked is a matter of “when” and not “if.” Attackers now use automation to carry out their attempts. Any network or device that connects to the internet has a high chance of being attacked. By adding more devices and endpoints to their networks, businesses essentially widen their attack surface.
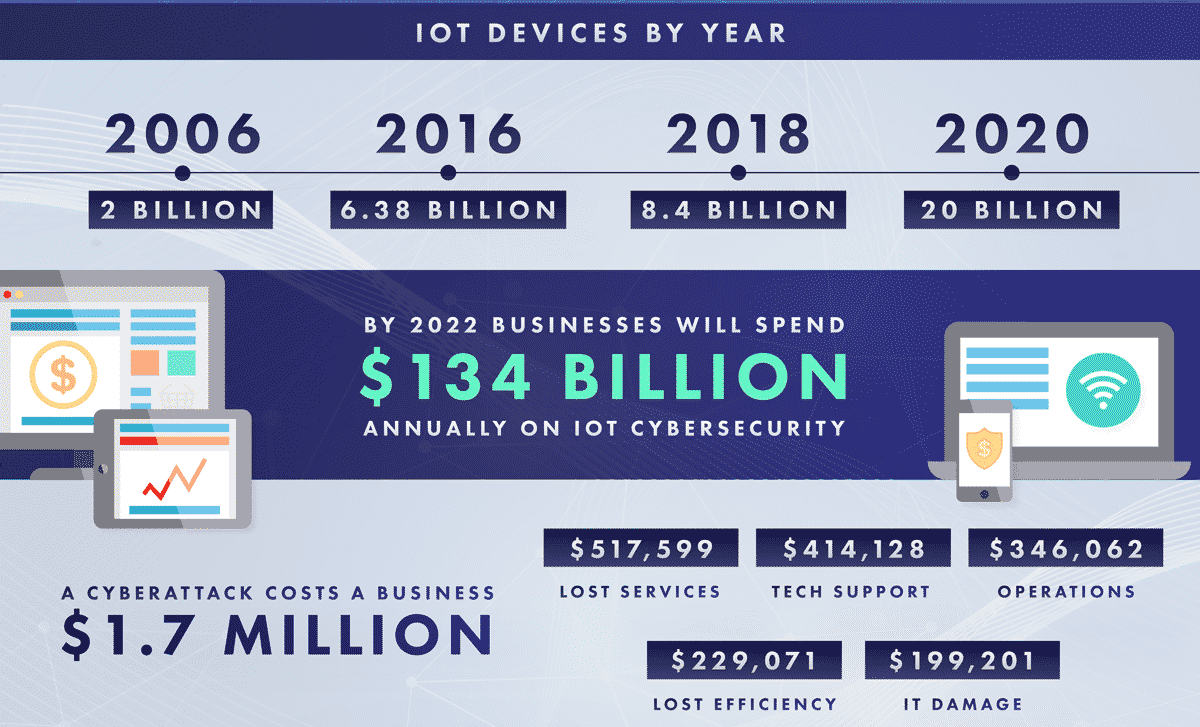
Source: Cloud Management Suite
By the end of 2020, analysts estimate that there will be more than 20 billion connected Internet-of-Things (IoT) devices. If you assume your corporate assets remain secure and untouched by IoT growth, you expose yourself to data breaches, overall outage, and loss of intellectual property. Hackers prey on the weakest link to access devices. Increasingly, these security holes result not just from email links, but smartphone apps, a quick check of social network status, smart sensors on the manufacturing floor, the automatic coffee pot in the break room, anything with access to the internet.
What kinds of threats can we expect?
Over the past years, the biggest attacks involved ransomware, data breaches, and DDoS attacks. We’re likely to see more of the same. Attackers now have control over botnets that could continuously carry out these attacks. Last January, the release of Collection #1 revealed that millions of username and password combinations are available in the black market likely obtained from previous breaches. Since users tend to reuse passwords, hackers can use these data to breach other systems.
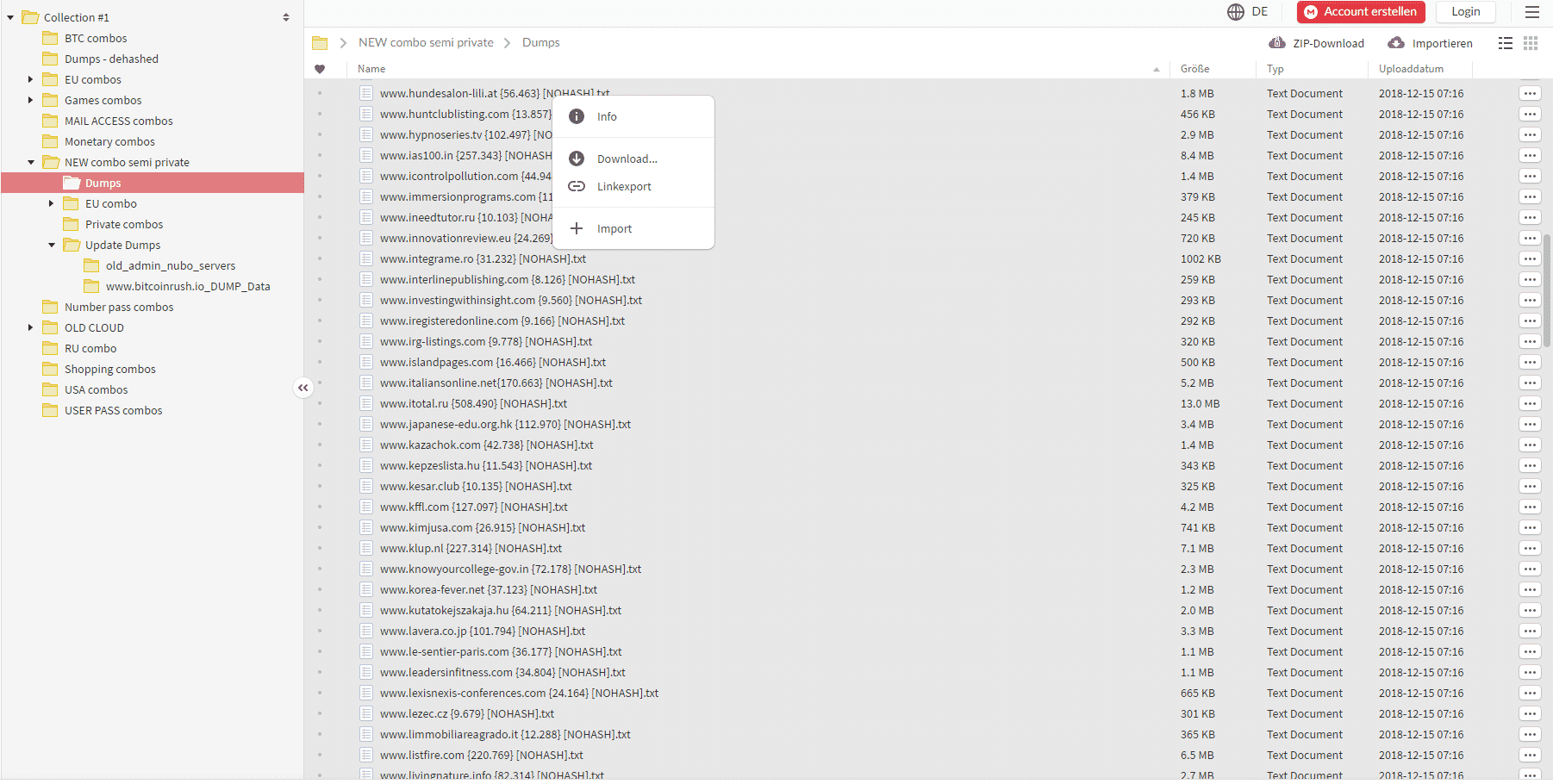
Source: Troy Hunt
Social engineering methods are also tried-and-tested means for hackers to gain access to systems. We could expect the continued use of phishing to try and fool users into installing malware, clicking on malicious links, and revealing access credentials. But we also have to be aware that attackers are evolving their methods. They continue to seek ways to exploit the weak links in the security chain.
What are some of these new methods that attackers use?
Hackers are always looking for vulnerabilities so there’s bound to be exploits that will be discovered and used for attacks. Some hacker groups are even experimenting with artificial intelligence to help them get around conventional security measures.
IoT devices have also become popular targets. Businesses and consumers are adopting smart devices at a rapid pace thanks to the deluge of cheap IoT devices entering the market. Unfortunately, many of these cheap gadgets actually lack essential security features making them vulnerable to attacks.
Another emerging threat is extortion through data protection laws. Attackers can threaten companies with data breaches or website defacement to make them non-compliant. Failure to protect private information can result in hefty fines from government agencies. In Europe, GDPR fines can cost as much as €10 million, or 2% of the worldwide annual revenue, whichever is higher. Attackers are banking on this fear to compel companies to pay ransom in exchange for not getting hacked.
How can companies can protect themselves?
There are a host of ways companies could secure their infrastructure from cyberattacks. Installing or enabling antivirus and anti-malware software on each endpoint is a start but this isn’t enough. Improving network security through firewalls prevents malicious traffic from reaching their networks. Educating staff on the proper use of resources and how to avoid falling victim to social engineering attacks also helps.
We at Cloud Management Suite provide a platform to empower users with comprehensive IT management capabilities. Administrators could easily manage any part of their infrastructure through the cloud. They must also know what devices are running on their network, where they are, and what software and processes their devices are running at all times. With a simple, clean, user interface we have abstracted the complexities of visualizing your network, present all possible access points, and flag devices with critical security vulnerabilities.
It’s also critical to have realtime security. If critical updates are released, patches must be immediately deployed to ensure that affected systems are kept secure. Our users could even take advantage of automated patch deployment to ensure that all devices, including IoT, are up-to-date and free from vulnerabilities.
Why does security have to be realtime?
Attackers are constantly probing networks so mitigation and response measures should be running 24/7. Attacks can happen in between scheduled updates and scans. If your data is an hour old and you aren’t tracking suspicious processes, your antivirus solution and firewall won’t protect you.
Our solution tracks roaming and IoT devices and can detect, in realtime, if a virulent process starts running on any desktop, laptop or server. In cases where some questionable processes are detected, administrators must be able to kill these processes or take affected devices offline.

Source: Cloud Management Suite
Attacks could be quite devastating. Just recently, email service provider VFEmail was hit by a catastrophic hack where the attacker was able to successfully wipe servers and backups. Even though it was detected in the middle of the attack, the damage was quite significant that the service fears that it may not be able to recover. I hope they do. But this just goes to show how determined and malicious hackers are.
All this sounds worrying, should companies be afraid?
Companies should definitely be concerned. Dealing with a cyberattack isn’t easy and smaller operations may find it hard to recover should they fall victim. But it’s also important not to be overcome by fear and panic. Cybersecurity threats are part of our reality today. The sooner we all accept this, the sooner we can move forward and take steps to prevent and react to these threats.
Fortunately, there are a wide variety of tools that are now available to deal with most threats. Cloud-based services even make it easy for smaller ventures to acquire the necessary management and security solutions to help them beef up their security.
Cybersecurity also requires a concerted effort from everyone. Companies should put security as a key part of their agenda and encourage vigilance and care from their members.
The post Prepare to Be Hacked: Why Realtime Security is Crucial in 2019 appeared first on TechWorm.
0 Response to "Prepare to Be Hacked: Why Realtime Security is Crucial in 2019"
Post a Comment